< Snort on Windows XP Pro SP2 | Java & Friends | Snort and MySQL Database >
Testing Snort on Windows XP Pro SP2
What do we have in this session?
-
Testing Snort from Windows Console
-
Testing Snort Config File
-
Running Snort from any Windows Path
-
Snort in Sniffer mode
-
Snort as Packet Logger
-
The Not Using PCAP_FRAMES message
Testing Snort from Windows Console
Save and close the snort.conf file. Launch Windows command prompt. Type:
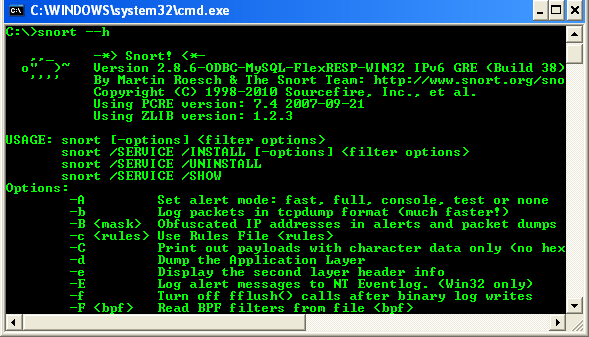
C:\>Snort\bin\snort --h or C:\>Snort\bin\snort -?
The command will invoke the Helps.

A complete Snort commands are shown below.
USAGE: snort [-options] <filter options>
snort /SERVICE /INSTALL [-options] <filter options>
snort /SERVICE /UNINSTALL
snort /SERVICE /SHOW
Options:
-A Set alert mode: fast, full, console, test or none (alert file alerts only)
-b Log packets in tcpdump format (much faster!)
-B <mask> Obfuscated IP addresses in alerts and packet dumps using CIDR mask
-c <rules> Use Rules File <rules>
-C Print out payloads with character data only (no hex)
-d Dump the Application Layer
-e Display the second layer header info
-E Log alert messages to NT Eventlog. (Win32 only)
-f Turn off fflush() calls after binary log writes
-F <bpf> Read BPF filters from file <bpf>
-G <0xid> Log Identifier (to uniquely id events for multiple snorts)
-h <hn> Home network = <hn>
-H Make hash tables deterministic.
-i <if> Listen on interface <if>
-I Add Interface name to alert output
-k <mode> Checksum mode (all,noip,notcp,noudp,noicmp,none)
-K <mode> Logging mode (pcap[default],ascii,none)
-l <ld> Log to directory <ld>
-L <file> Log to this tcpdump file
-n <cnt> Exit after receiving <cnt> packets
-N Turn off logging (alerts still work)
-O Obfuscate the logged IP addresses
-p Disable promiscuous mode sniffing
-P <snap> Set explicit snaplen of packet (default: 1514)
-q Quiet. Don't show banner and status report
-r <tf> Read and process tcpdump file <tf>
-R <id> Include 'id' in snort_intf<id>.pid file name
-s Log alert messages to syslog
-S <n=v> Set rules file variable n equal to value v
-T Test and report on the current Snort configuration
-U Use UTC for timestamps
-v Be verbose
-V Show version number
-W Lists available interfaces. (Win32 only)
-X Dump the raw packet data starting at the link layer
-x Exit if Snort configuration problems occur
-y Include year in timestamp in the alert and log files
-Z <file> Set the performonitor preprocessor file path and name
-? Show this information
<Filter Options> are standard BPF options, as seen in TCPDump
Longname options and their corresponding single char version
--logid <0xid> Same as -G
--perfmon-file <file> Same as -Z
--pid-path <dir> Specify the directory for the Snort PID file
--snaplen <snap> Same as -P
--help Same as -?
--version Same as -V
--alert-before-pass Process alert, drop, sdrop, or reject before pass, default is pass before alert, drop,...
--treat-drop-as-alert Converts drop, sdrop, and reject rules into alert rules during startup
--process-all-events Process all queued events (drop, alert,...), default stops after 1st action group
--dynamic-engine-lib <file> Load a dynamic detection engine
--dynamic-engine-lib-dir <path> Load all dynamic engines from directory
--dynamic-detection-lib <file> Load a dynamic rules library
--dynamic-detection-lib-dir <path> Load all dynamic rules libraries from directory
--dump-dynamic-rules <path> Creates stub rule files of all loaded rules libraries
--dynamic-preprocessor-lib <file> Load a dynamic preprocessor library
--dynamic-preprocessor-lib-dir <path> Load all dynamic preprocessor libraries from directory
--pcap-single <tf> Same as -r.
--pcap-file <file> file that contains a list of pcaps to read - read mode is implied.
--pcap-list "<list>" a space separated list of pcaps to read - read mode is implied.
--pcap-loop <count> this option will read the pcaps specified on command line continuously.
for <count> times. A value of 0 will read until Snort is terminated.
--pcap-reset if reading multiple pcaps, reset snort to post-configuration state before reading next pcap.
--pcap-show print a line saying what pcap is currently being read.
--exit-check <count> Signal termination after <count> callbacks from pcap_dispatch(), showing the time it
takes from signaling until pcap_close() is called.
--conf-error-out Same as -x
--enable-mpls-multicast Allow multicast MPLS
--enable-mpls-overlapping-ip Handle overlapping IPs within MPLS clouds
--max-mpls-labelchain-len Specify the max MPLS label chain
--mpls-payload-type Specify the protocol (ipv4, ipv6, ethernet) that is encapsulated by MPLS
--require-rule-sid Require that all snort rules have SID specified.
Testing Snort Config File
Let test the snort basic configuration that we have done. Run the following command. The meanings have been summarized in the following Table.
|
Option |
Meaning |
|
-c <rules> |
Use Rules File <rules> |
|
-l <ld> |
Log to directory <ld> |
|
-v |
Be verbose |
|
-i <if> |
Listen on interface <if> |
|
-T |
Test and report on the current Snort configuration |
C:\>Snort\bin>snort -c c:\snort\etc\snort.conf -l c:\snort\log -i2 -T

Running Snort from any Windows Path
In order to run snort and other related binaries, put the path in Windows environment variables and the steps are shown below.

Close any Windows console and re-open it. Run snort.exe from the root, C:\ drive.
Next, let have some story about Snort. Depending on your needs, Snort runs in three different modes: Sniffer, Packet Logger, and Network Intrusion modes.
Snort in Sniffer mode
If you’re running Snort from the command line with two network adapters, specify which adapter to monitor:
C:\>snort -v -i#
# is the number of the applicable adapters (as shown on the output of the snort -W command).
You must use this -i switch whenever you run the snort program on the command line. Sniffer mode is the simplest iteration of Snort. To run it, follow these steps: from the command line (within the %SnortPath%\bin directory and in our case, we can run it from any Windows path) type:
C:\>snort -v -i2
--------------------------------------------------------------
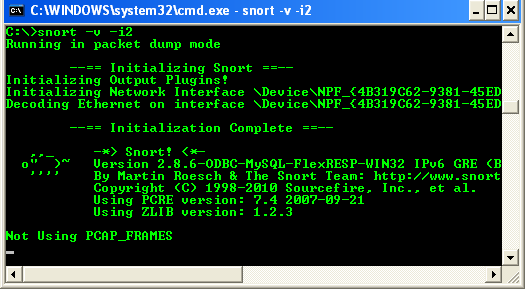
This command runs Snort as a packet sniffer with the verbose switch, outputting TCP/IP packet headers to the screen. Press Ctrl+C keys to stop the output. Snort/WinPcap summarizes its activities, as shown in the following screenshot.
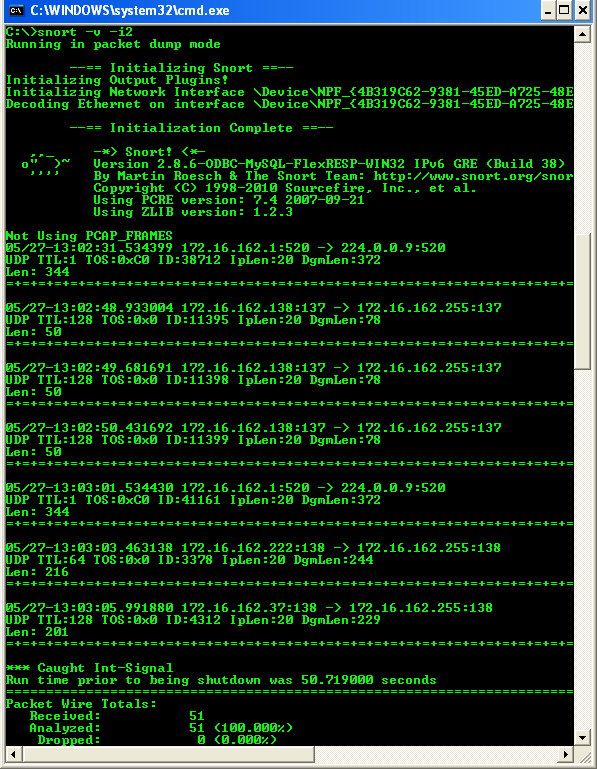
To receive a more detailed capture of packets on the wire, type:
C:\>snort -vd -i2

This command provides the TCP/IP headers and packet information (descriptive). Type snort at the command line for a full list of all the switches. If you’re getting TCP headers, you know that so far you’re right on track. If you have more than one network card in your Snort IDS system, type:
C:\>snort -W

This command determines how WinPcap has these adapters numbered, and is only available in the Win32 version of Snort.
Snort as Packet Logger
You can test Snort’s logging abilities with the -l (log) switch, by typing (take note on the order of the options):
C:\>snort -vde -l c:\Snort\log -i2

Please press Ctrl+C to stop.

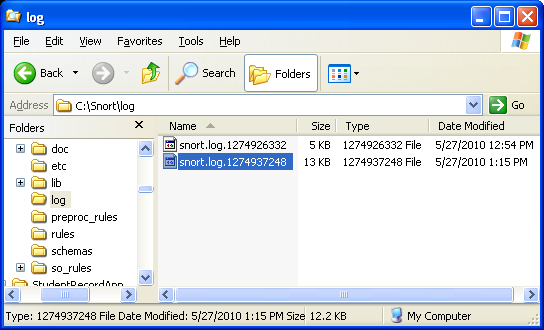
This runs Snort in descriptive verbose mode and logs all its findings to the directory called log under the Snort installation directory. The individual packets are filed in hierarchical directories based on the IP address from where the packet was received. Several command-line switches are specific to logging and output, including the ability to log all packets to a single binary file. Play around with those as needed.
The Not Using PCAP_FRAMES message
The Not Using PCAP_FRAMES message is normal. Try the following command:
C:\>snort -v -ix
Replace x with the number of the NIC which snort will use. If you’re using the wrong NIC 'pcap_frames' error will show up and if you use the right NIC pcap_frame error appears and just stays there until you have some traffic running through. So, make sure to use the right number of NIC when running snort. When running as a service, a valid and appropriate NIC number also must be specified.